- Destructuring is an ES2015 feature which allows binding variables to values inside arrays and objects.
-
let [a, b = 5, c = 7] = [1, 2] a === 1 b === 2 // default of 5 provided but not required c === 7 // default of 7 provided and required d === undefined // no default provided and no value
-
let { firstName, surname : lastName, address: { street } } = { firstName: 'John', surname: 'Smith', address: { street: '1 Happy Lane', postcode: 'HP1 1HP' } } firstName === 'John' lastName === 'Smith' // value of surname extracted into lastName street === '1 Happy Lane' // Street extracted from inner object // Postcode not extracted - These method are most useful when used within method arguments to save having to manually extract required properties from an object.
Azure N-series VMs (with GPUs)
Azure now offers N-series VM’s with 1, 2 or 4 dedicated GPUs which can be utilised for GPU optimised tasks such as graphic rendering, video editing and parallel computing.
- The NC VMs are targeted towards computing power, and the NV VMs are targeted towards on demand graphical visualisation
- The VMs are currently only available in some regions, like US east (Virginia)
- The VMs are currently only available for some OSes, like Windows Server 2012 R2 and Windows Server 2016
- The VMs are currently only available connected to an HDD
- The drivers are not installed by default, but can be found here. Once they’re correctly installed, the card(s) will be visible in device manager and GPU-Z
- GPU-Z currently has trouble reporting accurate utilisation, but nvidia-smi, usually found in C:\Program Files\NVIDIA Corporation\NVSMI\nvidia-smi.exe, offers a command line view of GPU utilisation:
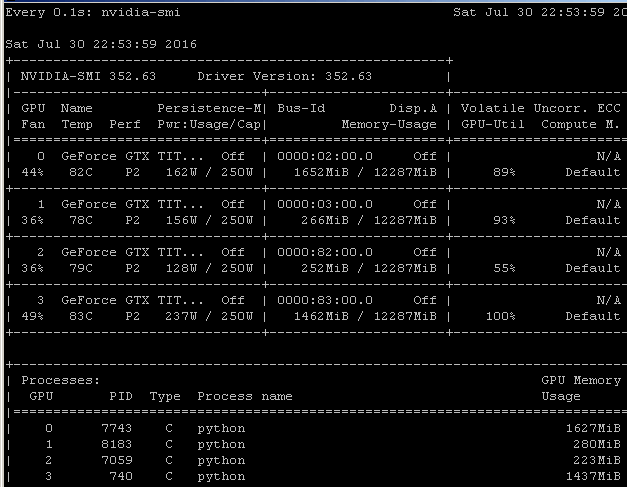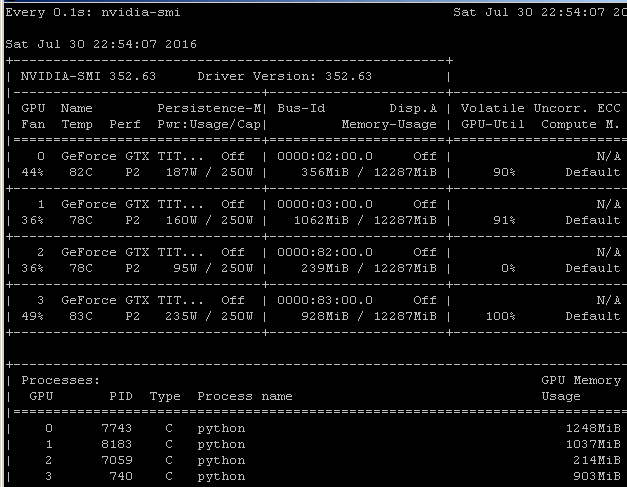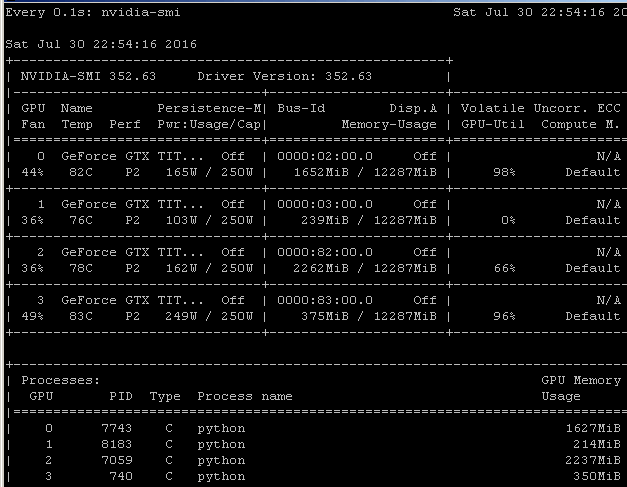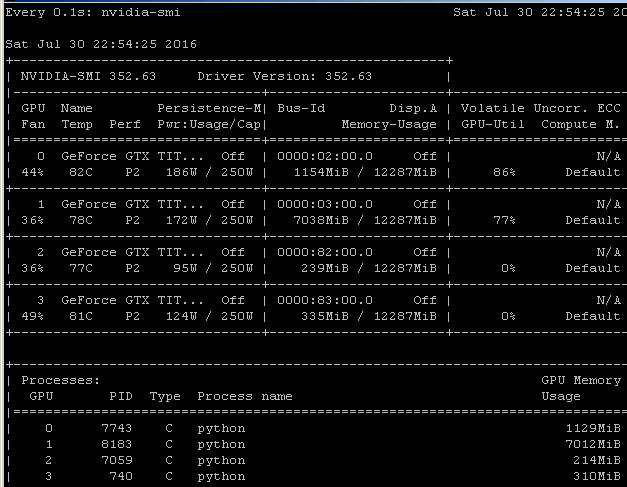
- The NC24 VM with 4 K80s is limited to 6 simultaneous video encoding processes
The Valet Key cloud design pattern
A Valet Key is a special key that some cars have which has limited functionality i.e. it only opens the driver’s side door and starts the engine, and does not open the glove box.
In the cloud, an application can issue an equivalent key, limited in scope and time, in the response to a request. The client then uses this key to access some other resource directly.
Benefits
- Issuing a key directly to the client means the request can return sooner, freeing up resources to handle other requests. This is especially beneficial when the operation is heavy or long running and would tie up considerable resources e.g. media transfer. Storage and data transfer are generally cheaper than computation.
- Keys can be issued with a convenient expiry time, allowing short bursts of communication to proceed with only the one initial server request.
Issues
- Although the keys can have fine grained scope to follow the Principle of Least Privilege, any compromise does nonetheless give an attacker full access to the resource within the scope and time limit.
- The potential attack surface is larger as it includes the resource itself, in addition to the issuing server and the key itself.
- Direct oversight of the resource is often lost. For example, it might not be possible to limit the size of an uploaded file, or gather download statistics.
Azure example implementation
- The upload file request hits the ASP.NET server, which does the lightweight setup of enabling CORS from the client browser, and retrieving a token from the blob storage.
- The browser can then upload the file directly to the blob.

Optimistic concurrency control
Optimistic concurrency control is a technique used for concurrency.
- It is used in databases and internally by concurrent data structure libraries
- It assumes that actions will generally complete without contention, so proceeds to perform the update immediately, then checks afterwards if the action can be committed or must be rolled back
- Avoiding the use of locks provides a performance boost, especially for .NET code where a lock could require an expensive entry into kernel mode
- Care must be taken in use and implementation, as high load can lead to increased contention, which increases the load etc.
Using an alternative namespace in LINQPad
LINQPad is a great tool which hides the complexity of a .NET app to allow fast development and testing of arbitrary pieces of code.
Unfortunately, it also hides the namespace definition, so it’s not possible out of the box to place a type in another namespace.
Fortunately there is a workaround, which consists of closing the implicit namespace which Main lives in, adding your custom namespace code, then opening a class EOF at the end:
void Main()
{
AlternativeNamespace.Foo.PrintNamespace();
}
}
namespace AlternativeNamespace
{
public static class Foo
{
public static void PrintNamespace()
{
Console.WriteLine($"Foo namespace: {MethodBase.GetCurrentMethod().DeclaringType.Namespace}");
}
}
}
class EOF
{
Output:
Foo namespace: AlternativeNamespace
Pets vs. Cattle
Pets vs. Cattle is an analogy used to emphasise the differences between the pre-cloud and cloud MOs, and a mindset shift which needs to be taken to make use of the elastic scaling capabilities of the cloud.

The real challenge is twofold:
The initial golden cow needs to be bred, from which you clone the rest of the herd.
This usually involves converting the current ephemeral state of servers and databases into concrete IaC (Infrastructure as Code) definitions, which can be used to stamp out new servers or database instances at will, in an automated fashion.
New genes need to be easily introduced into the gene pool.
This usually involves automating the release process, so changes to the IaC can be easily diffed, tested and deployed out to each server or database.
The other big benefit of cattle is that it becomes very easy for developers and testers to have their own prod-like environment, one per feature-branch, which can be created and deleted at will, quickly.
Azure Virtual Machine Scale Sets is Microsoft’s answer to stamping out cattle.
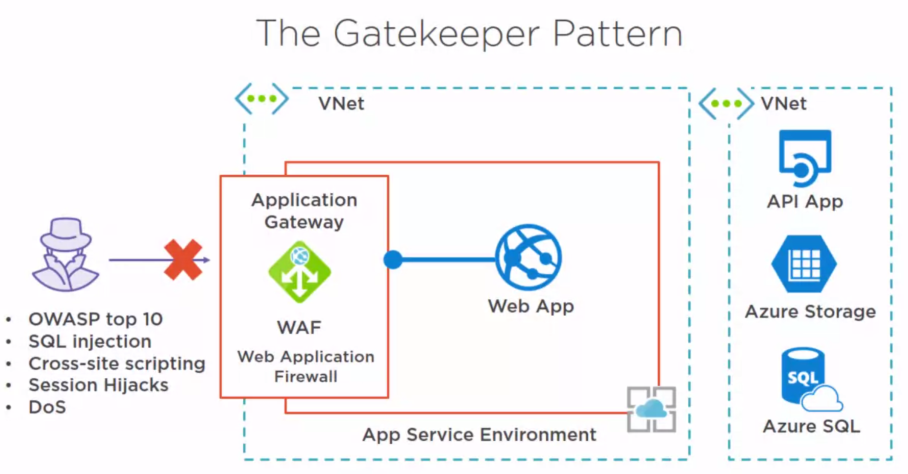
Gatekeeper cloud design pattern
The gatekeeper cloud design pattern protects an application by placing all services behind a single facade, similar to a firewall.
Benefits
- All services and data are private and hidden behind a single public endpoint, which significantly reduces the attack surface.
- Request validation and malicious communication rejection is implemented in a single place.
- The backend services can be optimised and scaled to handle legitimate requests only.
- If any breach does occur, the exposure is limited to the sensitive information on the gatekeeper itself, which should be kept to a minimum.
Issues
- The gatekeeper is a single point of failure for the entire application, and must be appropriately managed for high availability and redundancy.
- The gatekeeper may affect performance by increasing latency, increasing load and introducing a bottleneck.
Azure example implementation
- Place all backend services in a private virtual network.
- Place the web app endpoint in an App Service Environment which includes an Application Gateway, from which we can make use of the Web Application Firewall which blocks many common security vulnerabilities.
Culture aware DateTime formatting
There are various DateTime.ToString() format specifiers which are culture aware, which can be very useful to show the date in a native format, e.g. Christmas day 2017
| Culture | ToString(“d”) | ToString(“g”) |
|---|---|---|
| en-GB | 25/12/2017 | 25/12/2017 00:00 |
| en-US | 12/25/2017 | 12/25/2017 12:00 AM |
| en-CA | 2017-12-25 | 2017-12-25 12:00 AM |
However, note the ‘official’ format isn’t always that most used by the people – see en-CA above.
ConcurrentDictionary.GetOrAdd() facts
In any combination of any number of threads running for any values with the same key:
- It is guaranteed that only one item will be added
- and this will be the only call to which true is returned.
- It is not guaranteed that the delegate overload will only execute the delegate once
- because the class uses optimistic concurrency control.
- The implicit assumption is that it’s rare for multiple concurrent calls to occur in reality, so more efficient to compute anyway, then replace or throw away as appropriate.
- If the delegate is expensive or has unwanted side effects, a Lazy<> can be used instead.
Enable MySQL server query logging
- View current state of variables:
SHOW VARIABLES LIKE "general_log%";
- Set log location:
SET GLOBAL general_log_file = 'C:/Temp/QueryLog.log';
- Enable logging:
SET GLOBAL general_log = 'ON';
- Disable logging again (for improved database performance and disk usage):
SET GLOBAL general_log = 'OFF';